Oct 25, 2019 Scroll to the end of the dialog box to see the client credentials. Keep these values for pasting in our Citrix cloud Okta connections very soon. Click on the Citrix Cloud to Okta application and choose the option right hand side and click assign to groups. Choose “everyone” You will now see the option for everyone in groups for the application. Today, we are excited to announce that Okta’s solution has been verified as Citrix Ready with Citrix NetScaler Gateway to provide Single Sign On (SSO) capability using SAML, oAuth and RADIUS protocols to XenApp and XenDesktop Sites as well as any enterprise web application. Apr 17, 2021 Once Citrix NetScaler is deployed and configured with Okta, IT admins can manage access to cloud and legacy enterprise apps through a single pane of glass in the Okta admin console.

In the left hand tree under Citrix Gateway, select Virtual Servers. Locate the virtual server which you want to bind Okta RADIUS onto. Select the Edit button, as shown below. Scroll to the Authentication section and unbind any existing policies and close the Authentication sub-window.
This could happen due to SID mis-match specified at OKTA console in individual user’s SID attribute.
Additionally, you will see following error in DDC trace where DDC or Broker is unable to find or lookup the SID in Azure ADDS:
xxxxxxx,1,yyyy/mm/dd hh:mm:ss.xxxxx,xxxx,xxxx,x,BrokerDAL,1,Error,”AccountNameCache::TrySyncUniversalClaimsForAccount: ERROR SID:S-1-5-21-XXXXXXXXXX-XXXXXXXXXX-XXXXXXXXXX-XXXXXX not found using Identity API Exception:Citrix.Fma.Sdk.Identity.Interface.IdentityLookupFailureException: The lookup failed as the domain ‘S-1-5-21-XXXXXXXXXX-XXXXXXXXXX-XXXXXXXXXX’ could not be located —> Citrix.Fma.Sdk.Identity.Interface.IdentityNotFoundException: [customer id] Specified domain ‘S-1-5-21-XXXXXXXXXX-XXXXXXXXXX-XXXXXXXXXX’ was not found in: [Name:domainname.com NetBiosName:domainname SID:S-1-5-21-XXXXXXXXXX-XXXXXXXXXX-XXXXXXXXXX]
The Broker expects the user SID from Azure AADS and not the one from On-prem Active Directory
Related:
- No Related Posts
$auth = Get-STFAuthenticationService -Store (Get-STFStoreService -VirtualPath $storeVirtualPath)
$spId = $auth.AuthenticationSettings['samlForms'].SamlSettings.ServiceProvider.Uri.AbsoluteUri
$acs = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/AssertionConsumerService')
$md = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/ServiceProvider/Metadata')
$samlTest = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlTest')
Write-Host 'SAML Service Provider information:
Citrix Cloud Okta Login
Service Provider ID: $spIdAssertion Consumer Service: $acs
Metadata: $md
Test Page: $samlTest'
The sample output of the above command looks like this.
Netscaler Gateway App
SAML Service Provider information:
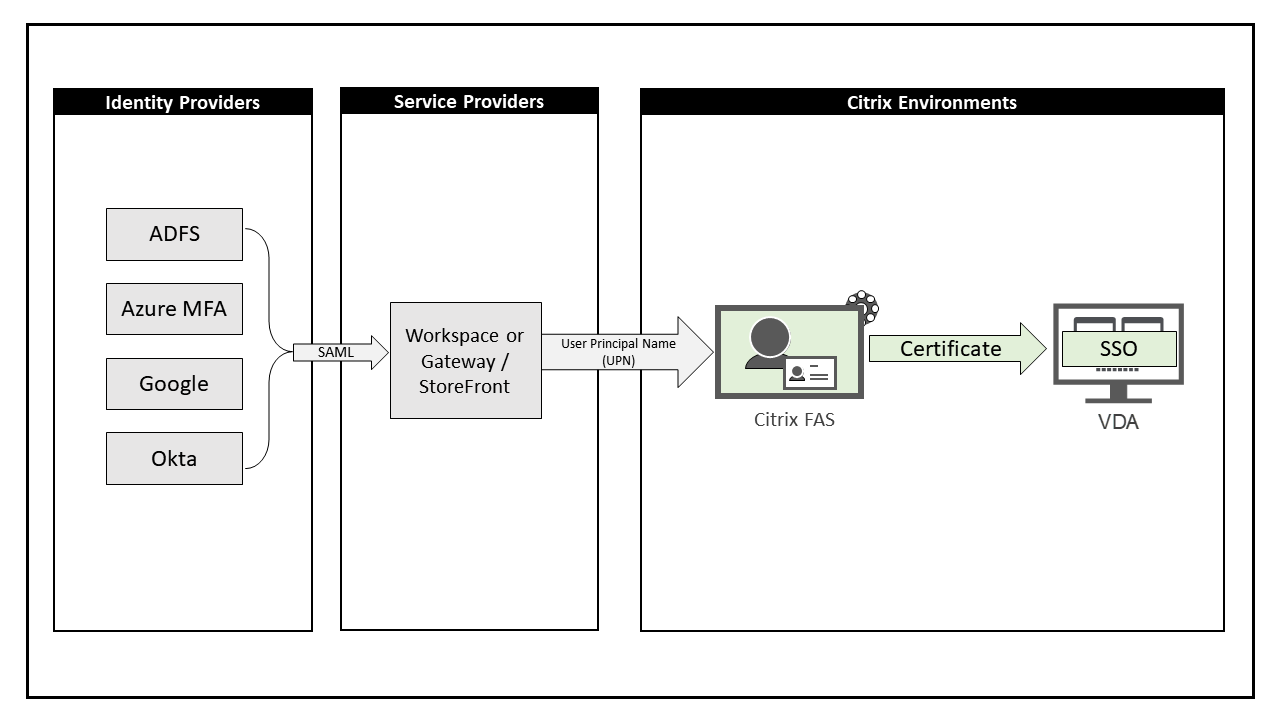 Service Provider ID: https://storefront.example.com/Citrix/StoreAuth
Service Provider ID: https://storefront.example.com/Citrix/StoreAuthAssertion Consumer Service: https://storefront.example.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService
Citrix Cloud Okta Login
Metadata: https://storefront.example.com/Citrix/StoreAuth/SamlForms/ServiceProvider/Metadata
Test Page: https://storefront.example.com/Citrix/StoreAuth/SamlTest

 Okta Configuration:
Okta Configuration:- On the Okta create a new application for the Web Platform with SAML 2.0 enabled.
- Once the new application is created follow the below steps to configure the SAML settings
Note:
- The Single Sign On URL in the above step should be the Assertion Consumer Service URL from the StoreFront Output.
- The Audience URI should be the Service Provider ID from the Storefront Output.
- Rest of the setting can be default.
- In the next step you can Preview the SAML assertion click on the link shown up in the below image.
- On the next step click on finish to the Service Provider configuration on the Okta.
- In the next step, click on the Sign On tab and edit the application user format to reflect AD User Principle Name
- Also click on the Identity Provider Metadata to download the metadata file which we will use in the Storefront Configuration steps below.
- In the next step assign the users to application on the Okta who will go through Okta to Storefront.
Storefront Configuration:
- On the Storefront, enable the SAML Authentication under the Manage Authentication Methods in the Storefront Console.
- Open an elevate PowerShell and run the below command to import the Okta metadata file.
Get-Module 'Citrix.StoreFront*' -ListAvailable | Import-Module
# Remember to change this with the virtual path of your Store.
$StoreVirtualPath = '/Citrix/Store'
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
 $auth = Get-STFAuthenticationService -StoreService $store
$auth = Get-STFAuthenticationService -StoreService $storeUpdate-STFSamlIdPFromMetadata -AuthenticationService $auth -FilePath 'File path of the metadata file you downloaded from Okta'
Note:
- Change this value for your Store.
- Also point the file path to the location where you saved the Okta metadata file.
- Now when you go to the Storeweb, you should get redirected to the Okta page for sign in.
Note: The above configuration will work with the Receiver for Web
Additional Resources
References for Configuring FAS:
https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-12/secure/federated-authentication-service.html
Disclaimer
